MCAI Culture Vision: Exposing the People Who Weaponize Institutions
How People Exploit Institutions to Isolate, Retaliate, Control, and What They Fear
I. Introduction: The Need to See Coordinated Harm
The name "Karenina Vision" by MindCast AI comes from the Anna Karenina principle, inspired by the famous line in Tolstoy’s novel: “All happy families are alike; each unhappy family is unhappy in its own way.”
In systems thinking, this means success requires alignment across many dimensions, while failure can come from the breakdown of just one. But what if failure isn’t random or messy? What if certain kinds of harm repeat because specific people know how to make institutions fail on purpose—quietly, and with deniability?
Some people exploit rules to retaliate. They hide behind process to exclude. They perform virtue to discredit those who speak up. When enough people do this together, using formal systems as cover, we don’t see harm—we see order.
Karenina Vision is a diagnostic framework for detecting that kind of harm: not random dysfunction, but coordinated exclusion that appears legitimate. The harms don't erupt through failure. They are executed by people who know how to work the system. We developed Karenina Vision to make those patterns measurable before they become culture.
II. The Four Mechanisms of Coordinated Harm
Insight: Coordination doesn't require intent—just repetition.
Each of the four mechanisms contributes to a modular system of harm. Each one allows individuals to act with plausible deniability while targeting others through formal channels. They’re deceptively simple, often hidden inside procedures or norms that seem fair on the surface. But when used together, they enable harm that feels systemic, even if driven by just a few people.
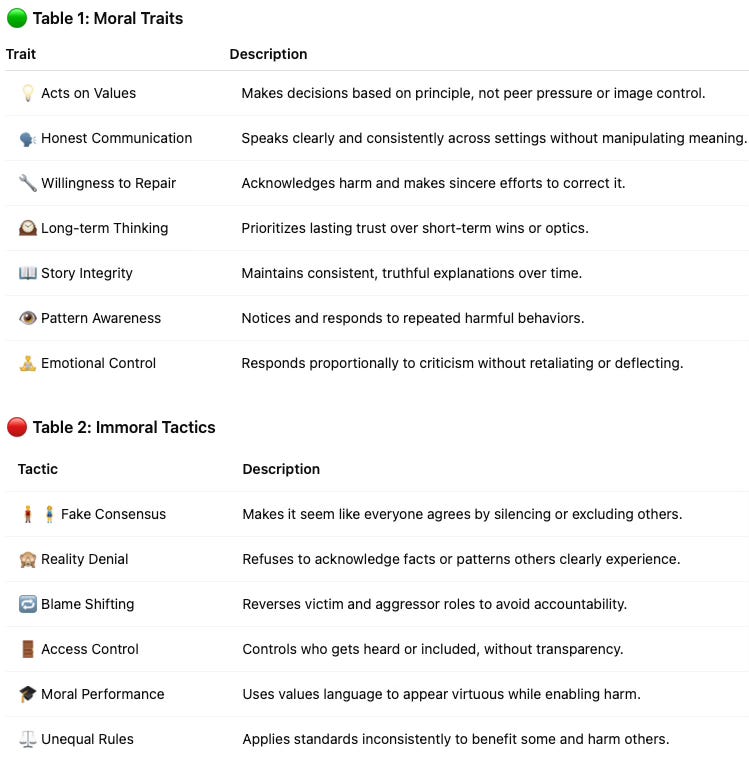
🧾 Manufactured Consensus – Pretending there is agreement by silencing or excluding dissent
🚫 Reality Denial – Ignoring patterns, evidence, and statistical documentation
🔄 Role Reversal – Painting the person harmed as the aggressor
🔐 Access Control – Controlling who gets to speak, influence, and be believed
The mechanisms are not theoretical—they are used by people, against people.
The four tactics create a logic of harm that feels like order. They allow coordinated retaliation to masquerade as professionalism. Once recognized, they reveal a shared language between people who claim no coordination at all.
III. Four Destructive Prototypes
Insight: Harm travels fastest through people who look like they belong.
Such prototypes thrive in what we call high-transmission environments—settings where influence, status, and messaging move quickly between people, but where structural accountability is slow, unclear, or actively suppressed. Examples include elite schools, foundations, social clubs, and professional networks. In these contexts, image is currency, and retaliation is executed through relationships, not rules. The illusion of professionalism is their shield—but once their pattern is exposed, their tower collapses because their power was built on reputation, not integrity.
Together, the four prototypes show how coordinated harm operates through roles rather than personality. Each one serves a function in the system of exclusion. When they work together, they create a complete loop of intimidation, isolation, and institutional cover.
⚖️ The Litigious Narcissist – Seeks to destroy others through process and escalation, often driven by generational dysfunction. This person uses lawsuits, complaints, and procedural attacks not just to win, but to break their target emotionally, socially, and reputationally. They thrive on conflict and often escalate it gleefully, interpreting the descent as confirmation of their narrative. Their goal isn't resolution—it's domination masked as professionalism. They rely on a veneer of formality to intimidate, exhaust, or discredit anyone who challenges them.
🎭 The Image Curator – Performs inclusion in public while coordinating exclusion behind the scenes. They speak the language of equity, collaboration, or community while privately suppressing dissent. Their influence depends on maintaining appearances while discrediting critics through soft power. Charm and public virtue are tools of control, not transparency. They rely on being seen as the moral center of a group while delegitimizing anyone who poses a reputational threat.
🧰 The Gatekeeper – Controls access to legitimacy, opportunity, and voice through social networks. They decide who gets heard, hired, promoted, or included. Their strength is relational, not positional—they shape the informal structures behind official decisions. Gatekeepers often operate through backchannels, making their power invisible but pervasive. They rarely issue harm directly, but enable it by deciding who never gets a chance to speak.
🏛️ The Institutional Mask – Provides bureaucratic cover to ensure no harm appears personal. They use process language and procedural rigor to shield coordination from scrutiny. Their decisions appear neutral and reasonable, even when outcomes reveal a consistent pattern of harm. Institutional Masks are critical to preserving deniability for the entire system. Their loyalty is not to truth, but to institutional image—ensuring nothing ever looks wrong from the outside.
These four prototypes show how coordinated harm is enacted through roles, not personality. Each one serves a function in the system of exclusion. When they work together, they create a complete loop of intimidation, isolation, and institutional cover.
What helps: Name the pattern, not the person. Focus on surfacing the structure rather than trying to expose intent. Patterns can be mapped and interrupted without relying on motive or confrontation. The more the behavior is framed systemically, the harder it becomes to hide behind performance or personality.
These prototypes are especially common in what we call high-transmission environments—settings where influence spreads quickly but accountability lags. These include elite schools, foundations, social clubs, and professional networks. In these contexts, image is currency, and retaliation is executed through relationships, not rules. The illusion of professionalism is their shield—but once their pattern is exposed, their tower collapses because their power was built on reputation, not integrity.
Their effectiveness lies in how they spread harm invisibly, under the cover of social or institutional legitimacy. Each one alone can do damage—but in combination, they replicate and protect one another. They aren’t just roles—they’re cover stories for retaliation. Naming them helps institutions recognize patterns they were never trained to see, but witness every day.
IV. How Karenina Vision Detects the Pattern
Insight: If harm keeps repeating, someone is maintaining the pattern.
Karenina Vision doesn’t prove motive—it maps behavior. It flags what’s missing (like repair or consistency) and what’s overused (like denial or manipulation). These signals reveal how coordinated harm is structured and sustained.
Detection doesn’t require surveillance—it requires pattern literacy. When we align observed behavior with known tactics, we reveal what’s being performed, concealed, or repeated. That turns the implicit into something explicit—and challengeable.
Karenina Vision evaluates two types of behavior patterns: moral traits that protect people from abusing power, and immoral tactics that allow harm to spread while appearing legitimate. What’s measured here isn’t theoretical—it’s behavior that either builds trust or corrodes it. Each set of traits gives us a clear view into how someone functions when their influence is challenged.
V. Scoring the Pattern
Insight: The most dangerous actors don't break rules—they master them.
Scoring reveals how much moral collapse or coordinated harm a person enables. We don’t look for motives—we look for configurations: which traits are missing, and which tactics are dominant. This gives us a composite score for each prototype. It also shows which behaviors are most predictive of deeper structural harm.
Scoring reveals how much moral collapse or coordinated harm a person enables. We don’t look for motives—we look for configurations: which traits are missing, and which tactics are dominant. This gives us a composite score for each prototype. It also shows which behaviors are most predictive of deeper structural harm.
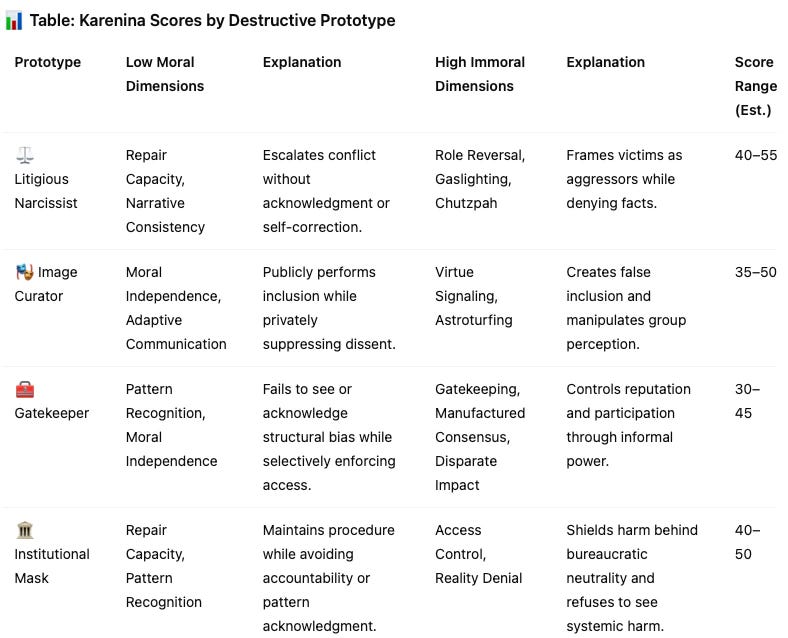
Moral scores reflect how consistently a person aligns with principles, maintains coherence, and demonstrates restraint under pressure. Litigious Narcissists tend to have low Repair Capacity and Narrative Consistency—they often escalate conflict without acknowledging harm. Image Curators collapse on Moral Independence and Adaptive Communication; their smooth exterior hides deep contradictions and strategic omission. Gatekeepers score poorly on Pattern Recognition and Independence, as they use social networks to selectively enforce access while pretending neutrality. Institutional Masks show low Repair and Pattern Recognition, repeatedly failing to act on known issues while maintaining procedural posture.
Immoral scores reveal where a person routinely violates norms of trust and fairness while appearing compliant. Litigious Narcissists score high on Role Reversal, Gaslighting, and Chutzpah—they frame themselves as victims while launching procedural attacks. Image Curators rely on Virtue Signaling and Astroturfing, creating a false sense of inclusion while coordinating exclusion. Gatekeepers activate Gatekeeping, Manufactured Consensus, and Disparate Impact—they exert control without transparency. Institutional Masks score high on Access Control and Reality Denial, enabling others’ harm while denying patterns and responsibility.
Each setting is scored across these dimensions. Higher moral traits and fewer immoral tactics indicate stronger alignment with ethical behavior. Karenina Score = (Avg. moral + (100 - Avg. immoral)) ÷ 2.
Karenina Scores translate abstract ethical dynamics into visible behavioral signatures. They show whether someone avoids accountability while appearing professional. They also show whether their power depends on truth, or on manipulation of process and perception. Low moral scores paired with high tactical use of harm reveal dangerous configurations.
VI. Intervention: What to Do When You See the Pattern
Insight: What you name, you can challenge.
Each mechanism of harm has a counter-tactic. Intervening doesn't require confrontation—it requires exposure. These strategies surface coordination while restoring fairness. The key is to interrupt repetition before it becomes culture.
📢 Break Manufactured Consensus – Require minority reports and reveal how dissent is handled. Surface hidden disagreement to challenge the illusion of unity. Coordinated exclusion depends on unchallenged silence. This tactic works best when used before decisions are finalized, not after. It also helps to document how dissent was excluded and who benefited from it. Surface hidden disagreement to challenge the illusion of unity. Coordinated exclusion depends on unchallenged silence. This tactic works best when used before decisions are finalized, not after.
📊 Counter Reality Denial – Show patterns with evidence and connect isolated cases to broader data. Build timelines, case comparisons, or longitudinal summaries. Visibility protects truth. Show that denial is not disagreement—it’s a refusal to confront what has already been seen. Consider visual aids or third-party audits to validate your findings. Build timelines, case comparisons, or longitudinal summaries. Visibility protects truth. Show that denial is not disagreement—it’s a refusal to confront what has already been seen.
🛡️ Prevent Role Reversal – Protect those who speak up from being portrayed as aggressors. Anticipate policy misuse and frame the issue clearly. Make retaliation predictable and legible. Keep the focus on documented behavior, not reputational distraction. Align with others who can confirm the sequence of events and intent. Anticipate policy misuse and frame the issue clearly. Make retaliation predictable and legible. Keep the focus on documented behavior, not reputational distraction.
🔓 Open Access – Publish selection criteria, rotate gatekeepers, and expose informal influence. Let access be verifiable, not assumed. Gatekeeping thrives where no one’s watching. Open systems reveal who benefits from silence and who gets left out. Make transparency a built-in expectation, not an afterthought. Let access be verifiable, not assumed. Gatekeeping thrives where no one’s watching. Open systems reveal who benefits from silence and who gets left out.
Each countermeasure works by disrupting one link in the chain. Intervening early makes coordination harder to sustain. Intervening visibly makes it harder to repeat. The more familiar we are with the pattern, the more easily we can break it.
But exposure alone isn’t always safe—especially in high-status environments where social retaliation is common. Intervention requires institutional cover, peer corroboration, and careful timing. Documentation, pattern analysis, and collective framing can protect individuals who take the risk to challenge harm.
The safest intervention begins with observation and pattern matching. Then comes documentation, reframing, and quiet coalition building. When formal reporting is used, it must be paired with external visibility and structural checks. Silence protects the coordination—so coordinated visibility becomes the counter-strategy.
VII. Conclusion: Coordination Is the Crime
Insight: When harm appears organized, it usually is.
What looks like dysfunction may actually be working exactly as intended—for the wrong people. Karenina Vision reframes harm as coordination, not accident. It names the behaviors and structures that allow people to exploit institutions while appearing legitimate. And it gives us a way to break that cycle before it becomes embedded.
The most dangerous actors in these systems don’t just avoid accountability—they fear exposure more than anything. Their strategies are designed to stay just inside the bounds of plausible professionalism. When surfaced, they rarely reflect or repair—instead, they double down, escalate, or invert the narrative. Their strength has never been tested under transparency—and they know it.
Once they lose control of the narrative, their power collapses quickly. Their reputational strength depends on keeping the story clean, controlled, and unrebutted. When others see the pattern and say it aloud, what once felt unchallengeable becomes hollow. And what was protected by silence becomes vulnerable to truth.
Once you see the choreography, it’s impossible to unsee.
Prepared by Noel Le, Architect of MindCast AI LLC. Noel holds a background in law and economics.