MCAI National Innovation Vision: Foresight Analysis in Illegal GPU Export Pathways (2025–2030)
How Third‑Country Routing, Regulatory Evolution, and AI Capability Laundering Will Reshape Global Compute Governance
See companion study MCAI National Innovation Vision: Foresight Simulation of NVIDIA H200 China Policy Exploits Vectors (Dec 2025).
Executive Summary
Seven days ago, MindCast AI identified Malaysia and Thailand as high-probability transshipment corridors where AI chips would be laundered through administrative identity transformation before reaching China. Aerospace’s Warning to AI, How Capability Laundering Will Reshape Corporate Compliance, Nov 14 2025. Yesterday, November 21, 2025, the Department of Justice validated that forecast: four individuals allegedly routed 400 Nvidia A100 GPUs through precisely these jurisdictions, using falsified declarations, shell companies, and document repackaging to evade U.S. export controls. US DOJ Release: U.S. Citizens and Chinese Nationals Arrested for Exporting Artificial Intelligence Technology to China, Nov 20 2025. The mechanics—false declarations, multi-layered intermediaries, opaque ownership chains—mirror the aerospace transshipment behaviors we documented last week, demonstrating that export-control vulnerability no longer lies in the physical movement of hardware but in the global diffusion of capability.
The core risk centers on architectural and firmware learning. Modern GPUs encode scheduling logic, HBM‑interposer design, microcode optimizations, and quantization pathways that cannot be cloned into a working replica yet meaningfully accelerate an adversary’s domestic GPU design by several years. Treating the DOJ case as a one‑off misunderstands its structural character: export‑control violations are no longer incidental—they are optimized, adaptive, and integrated within multi‑jurisdiction procurement networks.
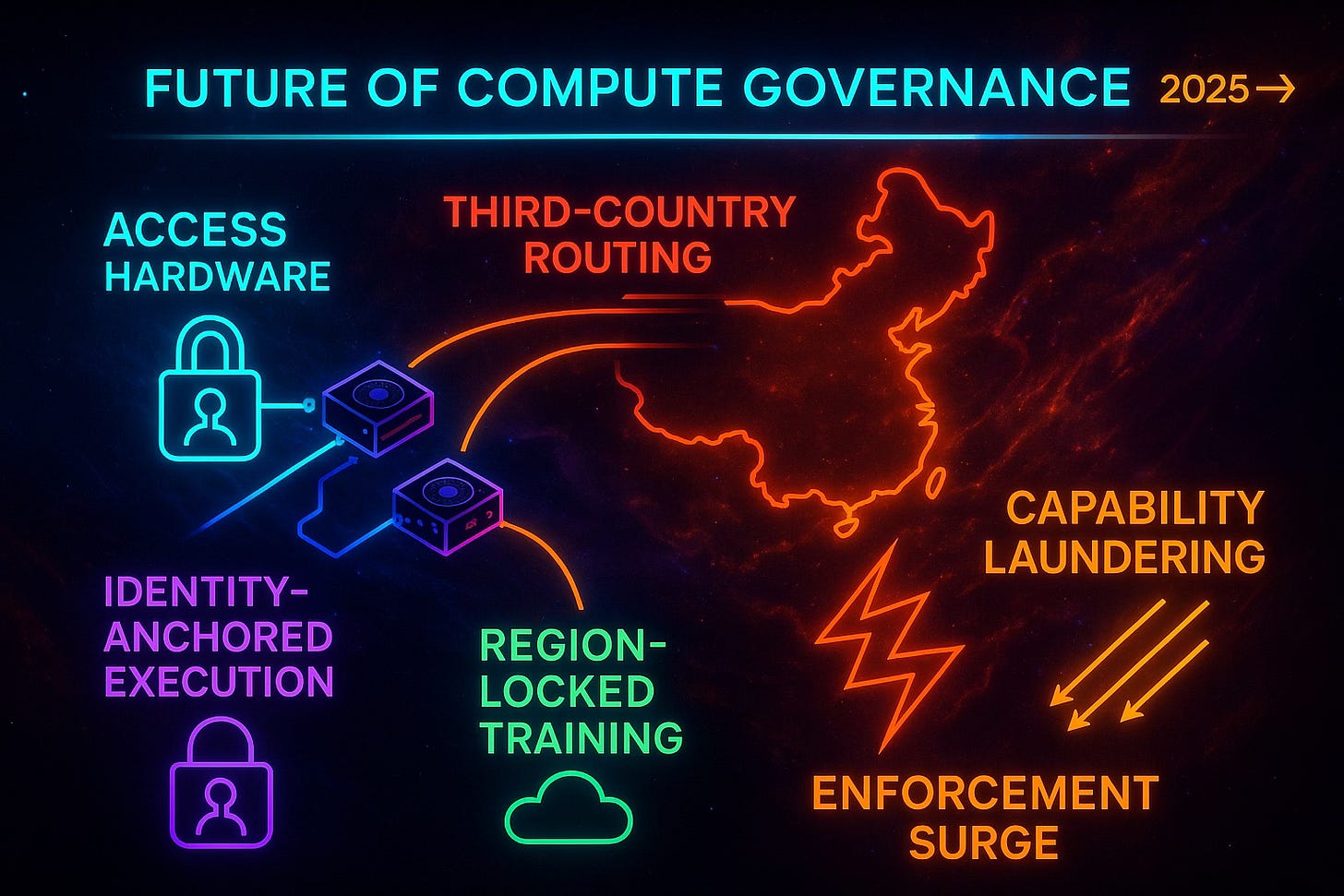
A Cognitive Digital Twin (CDT) model of the illegal routing chain identifies deliberate evasion behavior across Malaysia and Thailand—two jurisdictions that historically acted as aerospace transshipment hubs. Government‑side CDTs (DOJ, BIS, NSC) reveal a multi‑year regulatory realignment toward access‑layer governance: workload identity logging, compute‑access licensing, and region‑locked AI training environments. Firm‑side CDTs (NVIDIA, AMD, cloud providers) indicate an imminent pivot toward secure compute provisioning, distributor recertification, and identity‑anchored access controls. Ecosystem‑level modeling shows third‑country routing diversifying rather than shrinking.
By the late 2020s, global export‑control philosophy shifts from restricting hardware to governing who can run advanced compute, where, and under what identity. Firms that adapt early with access‑layer controls become trusted infrastructure; firms that delay face escalating remediation costs and regulatory fragility.
Relevance to Prior MindCast AI Work
The related analysis published by MindCast AI — Aerospace’s Warning to AI, How Capability Laundering Will Reshape Corporate Compliance — established the foundational insight that AI‑chip leakage follows the same structural patterns as aerospace technology diversion. That publication demonstrated how legal exports into friendly jurisdictions routinely transformed into indirect capability transfers to adversarial ecosystems through repackaging, joint ventures, and intermediary routing. The present foresight analysis builds directly on those findings, extending the aerospace framework into a real DOJ criminal case and showing how third‑country conductivity, beneficial‑ownership opacity, and identity laundering have now migrated into advanced‑compute governance. The DOJ case validates the earlier prediction that access—not hardware—would become the true locus of control.
Contact mcai@mindcast-ai.com to partner with us on National Innovation Policy foresight simulations. See also The Global Innovation Trap, Why Your R&D Investment Is Funding Competitors (Nov 22, 2025), MCAI Economics Vision: Synthesis in National Innovation Behavioral Economics and Strategic Behavioral Coordination (Dec 2025) discusses the relationship between MindCast AI’s two fall 2025 economic frameworks.
II. Incident Reconstruction and Leakage Topology
The Department of Justice indictment unsealed November 21, 2025 charges four individuals—including one U.S. citizen and three foreign nationals—with conspiring to illegally export approximately 400 NVIDIA A100 GPUs to China. The defendants allegedly received nearly $4 million to facilitate the scheme, which operated between October 2024 and January 2025 before law enforcement disrupted two additional shipments. Each faces up to 20 years under Export Control Reform Act violations. The charging documents detail falsified export declarations, shell companies in Malaysia and Thailand, and systematic mislabeling designed to evade Export Administration Regulations. Washington’s prosecution signals that GPU diversion constitutes not commercial violation but direct threat to technological advantage and enabler of military-relevant AI development.
The DOJ indictment reveals a sophisticated export-evasion architecture rather than a simple smuggling incident. The sequence begins inside the United States, where the originating exporter manipulated shipping classifications and exploited assumptions that GPU shipments resemble ordinary electronics. False declarations, undervaluation, and misleading tariff codes minimized inspection likelihood. These early actions functioned as the first deliberate maneuver in a larger, structured chain.
Once the hardware reached Malaysia, the operation shifted to identity alteration. Malaysian intermediaries—thinly capitalized entities with opaque ownership—repackaged the GPUs, replaced documentation, and introduced administrative distance between the shipment and its U.S. origin. Malaysia’s corporate and trade environment enabled this transformation: fast incorporation, minimal disclosure requirements, and logistics networks optimized for high volume rather than scrutiny.
Thailand acted as the normalization hub. Freight forwarders generated new export declarations that cleansed the shipment of its prior identity, making it appear as a standard Southeast Asian export destined for China. By the time the GPUs entered China, no document connected the hardware to the United States. The transformation was complete: a controlled item had been laundered through layers of administrative fiction.
This topology reflects a consistent export-evasion system: lawful origin, permissive intermediary, administrative normalization, and re-entry into a restricted ecosystem. The pattern is recognizable from aerospace leakage and now applies directly to advanced AI compute.
This physical export scheme complements the remote access vector we analyzed in our November 14 publication, where Chinese AI firms accessed Nvidia compute through Indonesian data centers. Together, these concurrent cases reveal capability laundering as a mature, multi-vector system: adversaries simultaneously exploit both digital access channels (Indonesia) and physical transshipment routes (Malaysia/Thailand). The pattern is not coincidental—it reflects systematic procurement architecture optimized for resilience.
III. Causation CDT Flow Mapping and Causal Signal Integrity Scoring
Causation modeling exposes the decision logic that drives persistent export‑control failures. Instead of a single linear violation, the flow reveals a multi‑node adaptive system with defined decision forks, incentive gradients, and substitution pathways. The U.S. exporter initiates the chain by manipulating documentation and exploiting low‑visibility shipping profiles. Malaysian intermediaries assume the next role, repackaging hardware and severing traceable identity markers. Thai consolidators finalize the transformation by generating administrative legitimacy that obscures the original export.
The Causal Signal Integrity (CSI) assessment follows the equation CSI = (ALI + CMF + RIS) / DoC², where DoC represents the degree of complexity in the routing chain. Action–Language Integrity (ALI) evaluates whether an actor’s stated intentions align with observable operational behavior; Cognitive–Motor Fidelity (CMF) measures the consistency between an actor’s decision-making logic and the execution patterns exhibited across the chain; and the Resonance Integrity Signal (RIS) assesses whether documentation, routing choices, and ownership structures propagate coherently across intermediaries. When these three components collapse simultaneously, the resulting CSI score signals a system engineered to defeat attribution.
The score of 0.031 arises from deeply inconsistent ALI, deliberate procedural deviation, and resonance patterns designed to frustrate traceability. A score this low reflects a chain optimized for opacity rather than convenience. CSI scores range from 0 (total opacity) to 1.0 (perfect traceability); scores below 0.05 indicate chains deliberately engineered for evasion rather than accidental compliance failures.
IV. Multi-Actor Trajectories and Ecosystem Dynamics (2025-2030)
Government Enforcement Evolution
Government CDTs reveal regulatory evolution from hardware-centric to access-layer governance. DOJ prosecutions and BIS designations of Malaysia and Thailand as elevated-risk corridors raise diversion costs while compelling distributor network reassessment. The critical shift: regulators increasingly require cloud providers to retain auditable workload-identity logs, track training intensities, and build compliance pipelines for forthcoming compute-access licensing regimes. Identity—not device possession—becomes the defining variable.
International coordination accelerates as Europe and Japan share U.S. concerns but lack common enforcement architecture. Modeling suggests convergence toward interoperable access controls: standardized workload logging, region-locked training zones, unified beneficial-ownership verification. By 2030, global regulation evolves from device-centric rules to identity-anchored access governance capable of tracking who runs advanced compute, where, and under what verified identity.
Corporate Adaptation Strategies
NVIDIA, AMD, and cloud providers confront a future where hardware sales alone cannot satisfy regulators or enterprise customers. Firms migrate toward secure, identity-verified compute services offering high-visibility execution environments rather than opaque chip distribution.
Distributor ecosystems contract as firms establish new trust baselines: transparent cap tables, ownership-verification processes, six-month recertification cycles. Cloud providers accelerate investment in identity-anchored workload routing, automated training-classification engines, and geo-fencing controls enforcing jurisdictional boundaries.
These shifts begin defensively but evolve into competitive differentiators. Regulators favor providers demonstrating visibility and control. Enterprise buyers prefer infrastructures reducing compliance exposure. Early redesign yields reputational advantages and regulatory trust; delay brings costly retrofits, reduced market access, and heightened scrutiny. Firms investing 15-25% more in access-layer controls between 2025-2027 avoid estimated $10-50M remediation costs when regulations harden in 2026-2027.
Ecosystem Conductivity and Chinese Networks
Southeast Asia functions as distributed routing web rather than isolated jurisdictions. Malaysia and Thailand remain primary corridors, but Indonesia, Vietnam, and Philippines offer parallel advantages: fast incorporation, limited beneficial-ownership disclosure, freight networks optimized for throughput over enforcement.
Chinese procurement networks exploit these openings through diaspora intermediaries, export-service brokers, and multi-tiered joint ventures obscuring ultimate beneficiaries. The system operates as resilient mesh—when pressure increases in one country, activity redistributes. Enforcement rarely eliminates pathways; it shifts traffic.
Without synchronized controls among U.S., Europe, and key Asian economies, new leakage corridors emerge as quickly as old ones close. Unilateral enforcement becomes whack-a-mole. Effective governance requires allied coordination establishing common compute-access standards, harmonized distributor verification, and shared intelligence on transshipment networks. The difference: allied coordination combined with access-layer controls—unlike hardware restrictions—cannot be circumvented through transshipment. Once compute workloads require verified identity regardless of physical location, the geographic arbitrage game collapses.
V. Long‑Range Foresight Through 2030
Long‑range modeling points toward a decisive shift in global governance of advanced compute. By the mid‑2020s, physical export enforcement intensifies, but policymakers and industry begin to recognize the limits of hardware‑centric controls. Jurisdictions that are adept at laundering administrative identities for goods become equally adept at obscuring the identity of compute workloads.
The inflection occurs in the latter half of the decade when export‑control regimes extend to training operations themselves. Regulators begin to require licensing for high‑intensity training workloads. Cloud providers respond by implementing region‑locked execution zones that prevent sensitive workloads from migrating into opaque jurisdictions. Identity becomes a core compliance layer—verifying not only who owns the compute resources, but who is running them and where.
China’s GPU development trajectory benefits indirectly from diverted hardware. Even without the ability to clone advanced GPUs, Chinese engineering teams extract insights through die imaging, x‑ray microscopy, circuit‑layer photography, firmware inspection, and packaging analysis. These techniques reveal memory‑controller strategies, tensor‑core scheduling patterns, interposer routing, thermal stack design, and HBM interface behavior. Reverse engineering does not produce a functional replica, but it accelerates learning curves by highlighting architectural tradeoffs NVIDIA already solved. Iteration—not replication—shortens China’s timeline for producing competitive accelerators, enough to alter longer‑term strategic balance.
By 2030, compute governance consolidates around three pillars: identity controls, access permissions, and jurisdictional segmentation. Export control becomes less about the movement of devices and more about regulating who can use advanced compute and under what conditions.
VI. Executive Actions and Policy Recommendations
Organizations face a narrowing window to modernize compliance infrastructure before regulatory requirements harden in 2026-2027. The shift from hardware-centric to access-layer governance demands immediate operational changes.
Corporate Actions:
Deploy workload-logging systems with identity verification: Implement comprehensive logging capturing who uses compute, from where, and for what purpose. Track authentication chains, geolocation data, and workload classifications in formats compatible with anticipated BIS reporting requirements. Early implementation avoids the $10-50M retrofit costs when quarterly audit mandates arrive in 2026.
Implement geo-fenced execution preventing cross-border training migration: Enforce jurisdictional boundaries at the orchestration layer. Region-lock high-intensity training workloads to prevent jobs from migrating to opaque jurisdictions mid-execution. This creates defensible compliance postures that regulators reward with expedited licensing and trusted-provider status.
Adopt automated training-classification engines: Monitor compute consumption patterns to identify export-controlled workloads—large-scale transformer training, multi-modal fusion, military-relevant applications. Real-time classification enables intervention before violations occur.
Establish six-month distributor recertification cycles: Recertification must include beneficial ownership mapping, verification of ultimate controlling parties, and assessment of non-allied equity stakes above 5%. Distributors unable to provide transparency should be removed from approved networks.
Monitor Southeast Asian risk corridors: Maintain continuous intelligence on regulatory changes, enforcement actions, and transshipment patterns across Malaysia, Thailand, Indonesia, Vietnam, and Philippines as baseline operational function.
Policy Recommendations:
Formalize compute-access licensing frameworks: Extend licensing requirements beyond hardware exports to training operations above defined compute thresholds. The regulatory trigger should be capability access, not device possession.
Standardize workload-logging formats: BIS should publish required data schemas, retention periods, and reporting frequencies. Standardization reduces compliance burden while ensuring efficient cross-provider analysis.
Mandate beneficial-ownership disclosure: All supply chain entities must disclose ownership structures identifying ultimate controlling parties through at least three corporate layers, flagging any non-allied ownership above 5%.
Establish third-country compute-risk tiers: Publish tiered risk assessments triggering corresponding compliance requirements: enhanced monitoring for Tier 2 jurisdictions, mandatory licensing for Tier 3. Clear guidance reduces compliance uncertainty.
Coordinate enforcement with allied governments: U.S., EU, Japan, and allies should harmonize compute-access regulations, share enforcement intelligence, and establish mutual recognition of compliance certifications to prevent jurisdictional arbitrage.
VII. Conclusion
The DOJ case unsealed November 21 validates the capability-laundering framework we published seven days earlier: AI chips migrate to restricted ecosystems through administrative identity transformation, using the same intermediary-routing tactics that once moved aerospace technology. Malaysia and Thailand function as predicted—deliberately selected jurisdictions offering logistical efficiency, regulatory opacity, and plausible deniability.
The convergence of two major cases within one week—Indonesia’s remote-access scheme and Malaysia/Thailand’s physical export operation—reveals that capability laundering has matured into systematic, multi-vector procurement architecture. Adversaries exploit both digital access and physical possession simultaneously, creating redundancy that ensures capability acquisition even when individual pathways face disruption.
Hardware-centric export controls cannot contain capability diffusion when compute access delivers the same developmental advantage as chip possession, and when transshipment corridors launder administrative identity faster than enforcement adapts. The shift toward access-layer governance—workload logging, compute licensing, region-locked training—represents recognition that export control must follow capability rather than devices.
The 2026-2027 inflection point remains on schedule. Organizations investing now in identity-anchored infrastructure will define the trusted compute tier regulators and enterprise buyers demand. Those delaying face not just retrofit costs but market exclusion as compliance becomes inseparable from commercial viability. Export control is becoming identity control, and the window to adapt is narrowing.