MCAI Economics Vision: Chicago School Accelerated — Integrated Application, Crypto ATM Liability Migration
Operator Accountability Under Behavioral Incapacity
See law and behavioral economics framing for this foresight simulation at MCAI Economics Vision: Chicago School Accelerated — Integrated Application, AI Hallucinations, AI Copyright, and Crypto ATMs (Dec 2025).
I. Introduction
The study functions as a companion to AI Copyright Liability Migration, which applies the same Chicago School Accelerated framework to AI systems. Chicago School Accelerated — The Integrated Framework (Dec 2025). Although the factual domains differ, both analyses exhibit identical causal structure: downstream actors cannot behaviorally self-protect, upstream actors control scalable prevention surfaces, and liability migrates accordingly. The crypto ATM domain provides a completed, non-speculative reference case for the liability trajectory predicted in AI copyright disputes.
Crypto ATM fraud persists because prevention costs less than extraction but misallocated liability systematically delays prevention. The resulting delay harms three audiences at once: victims subjected to live coercion, courts forced to allocate blame after the fact, and legislators confronting a problem that appears technical but remains structurally simple.
The foresight simulation applies MindCast AI’s Chicago School Accelerated methodology—an integrated modernization of Coase, Becker, and Posner with behavioral economics—to model liability allocation, predict regulatory outcomes, and identify where correction will occur. The framework addresses three constituencies simultaneously: judges deciding negligence and causation, regulators designing enforceable safeguards, and members of the public trying to understand why scams keep happening to ordinary people.
The core analytical move remains straightforward. When behavioral evidence demonstrates that disclosure fails to change behavior, liability must migrate away from actors who cannot prevent harm and toward actors who can. Crypto ATMs present a clean test case. Victims are often elderly or financially inexperienced, operating under live scammer coercion—frequently on the phone, under time pressure, and threatened with immediate consequences. In those conditions, warning screens and posted notices function as formalities, not protection.
Operators, by contrast, control transaction architecture. Operators set transaction caps, cooling-off periods, transaction holds, monitoring thresholds, and refund rules. Operators receive real-time transaction data and internal fraud alerts. Operators can intervene at low marginal cost, without guessing user intent or violating privacy. Once courts and regulators establish these facts, the allocation question shifts from moral or political terrain to doctrinal terrain.
The simulation integrates seven Vision Functions: Posner (liability allocation), Causation (CSI-gated causal integrity), Becker (incentive re-optimization), Coase (coordination infrastructure), Strategic Behavioral Cognitive (retailer exposure), Regulatory Vision (delay propagation), and Institutional Cognitive Plasticity (adaptation capacity). Each Vision Function produces quantified findings. Together the seven Vision Functions generate a trajectory with explicit time horizons, enforcement implications, and falsification criteria that courts, policymakers, and affected consumers can understand.
MindCast AI’s Cognitive Digital Twin methodology generates these findings by modeling the behavior of operators, retailers, victims, and institutions as interacting agents under legally and behaviorally constrained conditions.
II. Parties Modeled
Liability migration turns on who controls prevention surfaces, who bears learning costs, and who can adapt behavior at scale. Accordingly, Section II does not merely list actors; Section II specifies functional roles in the harm-production system and explains why those roles predict divergent exposure once liability reallocates upstream. The relevant distinction is not moral blame or formal job title, but architectural position: who designs systems, who intermediates transactions, and who experiences harm without realistic exit or self-help.
The actors modeled below occupy asymmetric positions along the harm-production architecture. Some actors possess real-time control, data aggregation, and modification authority. Other actors participate passively or episodically, encountering the system only at the moment harm occurs. Institutions differ again, not by intent, but by coordination capacity and adaptation speed. Capacity and adaptation asymmetries determine where liability can produce deterrence and learning—and where liability cannot.
Operators
Bitcoin Depot, CoinFlip, and Athena Bitcoin design and control the transaction environment. The three operators set transaction caps, cooling-off delays, monitoring thresholds, settlement timing, and refund policies. The three operators receive real-time transaction data and aggregate fraud signals across thousands of machines, giving operators systemic visibility unavailable to any individual victim or retailer.
Retail Hosts
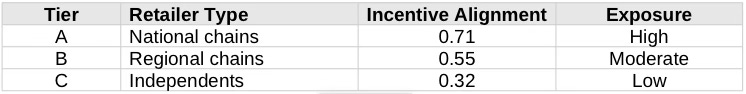
National convenience-store chains, regional chains, and independent stores fall into three tiers based on revenue-sharing structure, documentation density, and compliance centralization. Retail hosts do not design transaction architecture, but retail hosts do intermediate placement, visibility, and consumer trust. Retailer exposure varies sharply with contracting structure and internal governance.
Victims
Individual consumers, often elderly or financially inexperienced, encounter crypto ATMs episodically and under coercive conditions. Victims lack system-level information, cannot observe aggregate fraud patterns, and cannot cost-effectively verify or reverse transactions once initiated. Victim behavioral incapacity constitutes a binding constraint rather than a situational failure, and establishing behavioral incapacity as a binding constraint proves critical to the liability analysis.
Institutions
State legislatures (Washington, California, Illinois as primary analogs), state attorneys general, consumer protection agencies, and trial courts differ in coordination capacity, enforcement tools, and speed of response. Capacity and speed differences shape timing rather than direction of outcomes and explain why enforcement and private adjustment often precede statutory clarity.
Having established who occupies each architectural position, the simulation now models how Posnerian liability allocation operates when one party—the victim—cannot behaviorally self-protect.
Simulation Architecture: Cognitive Digital Twin Framework
The analysis that follows reflects outputs of a Cognitive Digital Twin simulation in which operators, retailers, victims, and institutions are modeled as distinct agents with asymmetric information, control surfaces, and adaptation speeds. Liability allocation is evaluated not in isolation, but as a system-level intervention whose effects propagate through incentives, coordination, and institutional response over time.
Contact mcai@mindcast-ai.com to partner with us on law and behavioral economics foresight simulations.
III. Posner Framework—Liability Allocation Under Coercion
Liability analysis begins with capacity rather than intent. Before incentives, coordination, or regulation matter, the law must determine who could realistically have prevented the harm under real-world behavioral constraints. Posner’s lowest-cost-avoider principle supplies that determination, but only once courts treat behavioral incapacity as a binding constraint rather than a factual afterthought.
Crypto ATM scams force the capacity question cleanly. Victims do not merely fail to exercise care; victims become structurally unable to exercise care once coercion begins. At the same time, operators are not peripheral intermediaries; operators design, control, and monetize the transaction architecture through which harm predictably flows. The asymmetry—total downstream incapacity paired with upstream architectural control—anchors everything that follows.
III.A Behavioral Incapacity of Victims Under Coercion
Crypto ATM scams defeat self-protection not through ignorance, but through coercion. Most scams begin before a victim reaches the machine: a phone call, text, or email creates urgency, fear, and perceived authority. Scammers often instruct victims to remain on the phone, warn victims that interference signals guilt or danger, and pressure victims to act immediately.
Under coercive conditions, behavioral economics predicts disclosure failure. Attention narrows, authority cues dominate, and victims discount warning information. Empirically, disclosure fails approximately 81 percent of the time under live coercion. Warning screens and posted notices function as formalities, not safeguards.
Courts already recognize coercion dynamics in doctrines of undue influence, duress, and fraud. Expecting victims to self-interrupt under coercion misallocates responsibility to the party least capable of prevention.
III.B Lowest Cost Avoider Analysis
Operators control the transaction environment. Operators set transaction caps, cooling-off periods, transaction holds, monitoring thresholds, and refund rules. Operators receive real-time transaction data and aggregated fraud reports across thousands of machines. Operators can intervene without identifying user intent at the point of sale.
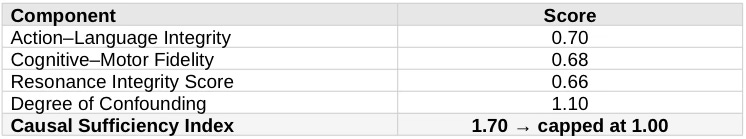
Operator avoidance costs register as low. On a normalized scale, prevention burden registers at 0.18. Victim avoidance capacity approaches zero once coercion begins.
Addressing the Operator Inability Defense
The strongest operator counter-argument is not lack of warning, but claimed inability to distinguish legitimate users from coerced users in real time without creating friction that drives customers to competitors. The argument misstates the design choice. Safeguards such as transaction caps, cooling-off periods, and delayed settlement do not require identifying coercion. Transaction caps, cooling-off periods, and delayed settlement limit the damage coercion can cause and apply neutrally to all transactions.
Friction at the margin is not a defect. Friction is the mechanism by which loss reduces. Daily withdrawal limits operate on the same principle across the banking system.
Hand Formula (Explicit)
• B—Burden of prevention: approximately $30–$70 per kiosk per year for software-based caps, delays, holds, and monitoring.
• P × L—Probability multiplied by loss: typically $3,000–$10,000+ per kiosk per year in scam-dense jurisdictions.
Because B ≪ P × L, continued operation without safeguards once on notice breaches the negligence threshold. The negligence conclusion follows from cost, control, and neutral design constraints rather than subjective intent assessment.
III.C Causation as a Posner Gate
Causation operates as a filter, not a rival doctrine. The question is whether assigning liability upstream remains structurally fair given how harm occurs.
Capping CSI at 1.00 is intentionally conservative. Even so, causation clears threshold. Third-party scammers do not sever the causal chain where operators possess knowledge, control, and financial benefit. Sony-style defenses fail; Napster-style secondary liability survives.
III.D Posner Conclusion
When harm predictably flows through a controlled system, liability migrates to the party best positioned to prevent harm, regardless of third-party exploitation.
The Posnerian allocation does not end the inquiry. The allocation triggers predictable responses from market participants and institutions, which determine how quickly correction occurs.
Section IV now examines how private actors respond once they perceive the liability shift that Posnerian analysis predicts.
IV. Market Response to Posnerian Liability Pressure
Once liability allocation shifts upstream, private actors do not debate doctrine; private actors adjust behavior. Incentives realign, contracts move, and exit or adaptation decisions follow predictably.
IV.A Operator Re-Optimization
The operative question is whether operators exit or adapt. Behavioral drift registers at 0.74, switching costs at 0.41, and margin compression tolerance at 0.62. Behavioral drift, switching cost, and margin compression values predict adaptation rather than mass exit. Claims that safeguards threaten business viability function as strategic positioning and remain empirically falsifiable.
IV.B Retailer Movement as Early Signal
Retailers often move before operators. National chains face the highest exposure due to centralized contracting, documented revenue-sharing ($300–$700 per kiosk per month), and internal compliance memoranda.
IV.C Transmission Mechanism
Liability pressure propagates contractually. Indemnity clauses tighten, revenue shares compress, audit rights expand, and select retailers exit kiosks. Private contractual adjustments often precede formal regulation.
The speed of market response contrasts sharply with the pace of public institutions, creating a gap that explains why harm can persist even after liability logic becomes widely understood.
Section V analyzes why institutional response lags market adjustment and identifies where delay compounds harm.
V. Institutional Delay in Applying Posner
Clear liability allocation does not guarantee immediate correction. Institutional response unfolds more slowly, shaped by coordination costs, procedural friction, and asymmetric adaptation speeds. Section V consolidates analytical layers that, in a longer technical version, would appear as separate treatments of coordination infrastructure, regulatory delay mechanics, and institutional adaptation capacity.
V.A Coordination Failure
Absent harmonization, operators arbitrage state borders. Coordination capacity sits at 0.57—too high for collapse, too low for equilibrium. Focal-point integrity has degraded to 0.44. Individual states acting alone bear disproportionate enforcement costs while benefits diffuse regionally, slowing adoption.
V.B Procedural Delay
Delay manifests through routine legislative mechanics rather than overt opposition. Legislators remove or raise transaction caps in committee. Floor votes narrow refund mandates. Effective dates push back 12–24 months. The delay propagation index registers at 0.76.
Delay is not neutral. Each month without safeguards produces predictable losses. Victims harmed during delay windows become casualties of timing, not ignorance.
V.C Institutional Adaptation Asymmetry
Advocacy groups adapt slowly. Institutional Update Velocity for legislative advocacy registers at 0.22, compared to 0.66 for legislatures and enforcement agencies. Pressure applied directly to lawmakers and attorneys general produces faster movement than engagement with intermediary advocacy structures.
V.D Federal Preemption as a Boundary Condition
Federal preemption does not change the direction of liability migration, but federal preemption alters migration speed and distribution. A strong federal floor that mandates transaction caps, cooling-off periods, and refund obligations would accelerate correction by eliminating interstate arbitrage and reducing coordination costs. A weak or disclosure-only federal regime would likely decelerate correction by freezing inadequate safeguards in place and preempting stronger state action.
Preemption therefore functions as an accelerant or brake depending on content, not as a neutral overlay. The fastest correction path remains state-led convergence followed by federal codification of proven safeguards.
V.E Tipping Conditions
Once one or two large states enact enforceable safeguards, delay becomes harder to justify. Complaint velocity (0.62) outpaces statutory adoption (0.59) and judicial citation (0.51). Template sharing through national attorney general networks accelerates convergence. Posnerian liability allocation propagates system-wide.
V.F Legislative Timing and Peer-State Sequencing (2025–2026)
Timing matters as much as substance. The liability migration described above interacts directly with legislative calendars, creating predictable sequencing effects.
2025 calendar year. California and Illinois function as validation states. If either state enacts additional safeguards—such as binding transaction caps, mandatory cooling-off periods, or refund obligations—during the 2025 legislative year, those enactments serve as live proof that safeguards remain administrable without market exit. Proof of administrability travels quickly through attorney general networks, legislative staff channels, and committee testimony templates.
Inter-session window (late 2025). During the period between adjournment and bill prefiling, alignment framing solidifies. Washington policymakers enter drafting cycles with peer-state language already tested. Operator claims of infeasibility lose force once comparable jurisdictions have implemented similar rules.
2026 Washington session. Washington’s 2026 session opens with alignment, not experimentation, as the dominant frame. Committee debate shifts from whether safeguards can work to whether Washington should remain an outlier. Amendment pressure remains, but the political cost of delay increases once peer-state outcomes become observable.
Early peer-state enactment explains why downstream correction accelerates even before formal federal involvement. Legislative calendars convert isolated state action into regional momentum.
Section X converts the preceding analysis into registered predictions with explicit time horizons and falsification conditions.
X. Predictions and Falsification Criteria
Foresight claims require more than narrative plausibility. Foresight claims require observable commitments that can succeed or fail on a defined timeline. Section X converts the preceding analysis into registered predictions with explicit horizons and falsification conditions, separating structural insight from retrospective explanation.
The predictions below do not assume regulatory enthusiasm or judicial innovation. The predictions follow mechanically from the Posnerian allocation established above, combined with observed incentive re-optimization and institutional delay patterns. Each prediction reflects forward simulation of the Cognitive Digital Twin under the liability allocation established in Section III. If liability migrates as predicted, these outcomes should appear in sequence. If the outcomes do not appear, the framework requires revision.
West Coast statutory alignment: 12–24 months.
Failure condition: Washington bill dies in Rules despite peer-state enactment.
Retailer contract renegotiation: 6–18 months post motion-to-dismiss survival.
Failure condition: No contract changes following adverse trial-court rulings.
Advocacy pivot: 3–9 months post peer-state enactment.
Failure condition: Continued categorical opposition despite enacted precedent.
Global falsifiers:
• Mass operator exit falsifies Becker predictions.
• Judicial rejection of architectural causation with CSI ≥ 0.8 weakens Posner allocation.
Section XI translates the analysis into actionable guidance for policymakers, litigators, and affected individuals.
XI. Applications
The analysis above explains why crypto ATM scams persist and where liability migrates. Section XI translates those findings into action—showing how courts, regulators, and the public can use the same structural insights to change outcomes rather than merely respond to harm after harm occurs. The goal is not awareness for its own sake, but leverage.
Policy
Transaction caps, cooling-off periods, and refund obligations are absorbable safeguards, not existential threats to the industry. California demonstrates feasibility. Operators remained in the California market after implementation, falsifying claims that basic protections threaten business viability.
For legislators, the critical move is framing. Legislators should position bills as alignment with peer-state precedent rather than experimentation. Alignment framing reduces amendment pressure, shortens narrative latency, and raises the political cost of delay. Effective dates matter as much as statutory language. A safeguard delayed is a safeguard denied.
Litigation
For plaintiffs’ counsel and attorneys general, early framing proves decisive. Counsel should establish architectural control at the outset: operators had knowledge, real-time intervention capability, and financial benefit tied to transaction size. Discovery should focus on transaction-monitoring systems, internal fraud reports, refund policies, and communications with retail hosts.
Retailer targeting should prioritize Tier A national chains with centralized contracting and documented revenue-sharing. National chains move first under litigation pressure and often drive broader compliance through contract renegotiation. Timing matters. Filing before operators rewrite indemnity clauses preserves leverage.
What Victims Can Do That Actually Changes Outcomes
Victims often feel powerless after a crypto ATM scam. Individual recovery remains difficult. Collective impact, however, proves real—and collective action shapes liability, regulation, and enforcement.
File complaints, even if funds are not recoverable. Complaints to state attorneys general, consumer protection agencies, and financial regulators are not symbolic. Complaints establish notice, quantify harm, and populate the datasets regulators rely on to justify enforcement and legislation. Unreported scams are invisible scams.
Preserve evidence. Transaction receipts, machine location, operator name, phone numbers scammers used, and any communications received matter. Patterns emerge only when details accumulate across cases.
Identify the machine operator and retail host. Many victims assume the scammer is the only relevant actor. In reality, accountability often turns on which company operated the machine and which retailer hosted the machine. Operator and host identification connects individual harm to systemic responsibility.
Understand timing. Victims harmed during regulatory delay windows are not outliers. Victims harmed during delay windows are foreseeable casualties of postponed safeguards. Public pressure focused on effective dates and implementation timelines—not just bill passage—changes legislative behavior.
XII. Conclusion
Crypto ATM scams are not inevitable features of new technology. Crypto ATM scams persist because responsibility has been placed on those least able to prevent harm and delayed for those best positioned to stop harm. Courts, regulators, and the public each have roles to play—but only when action targets structure rather than symptoms. When victim experiences are aggregated, documented, and timed to enforcement windows, victim experiences become catalysts for correction rather than isolated losses.